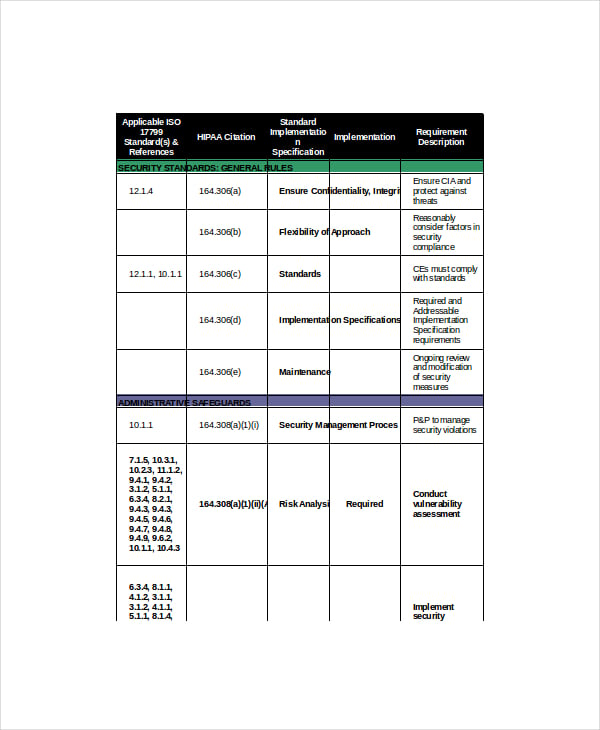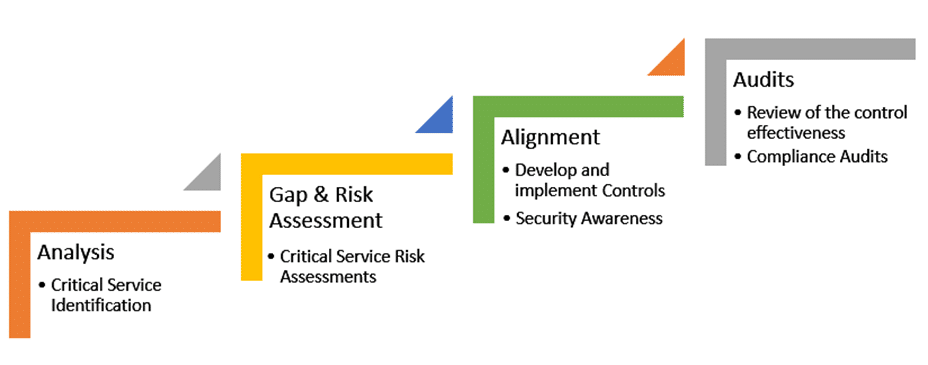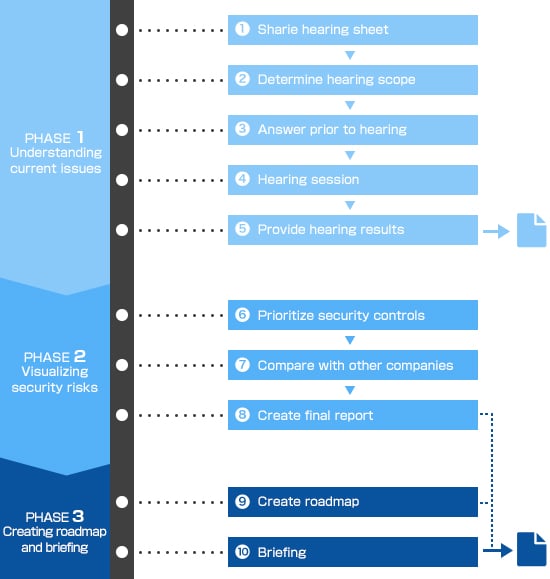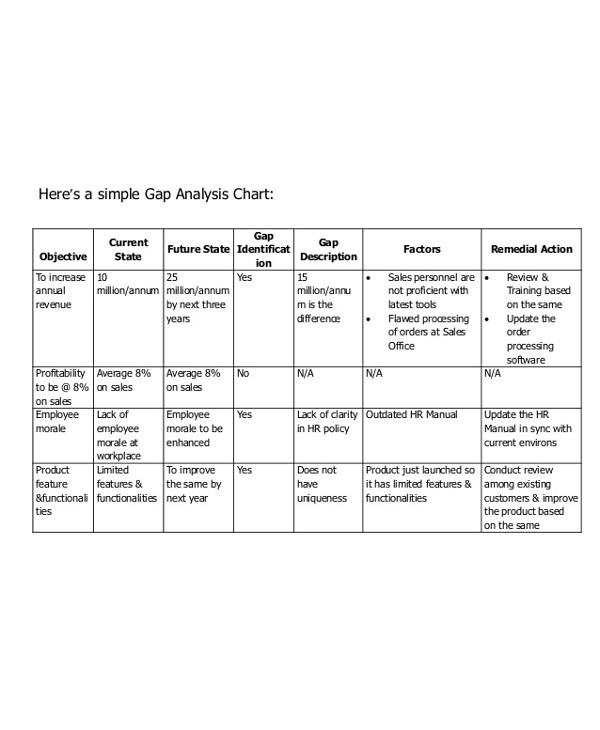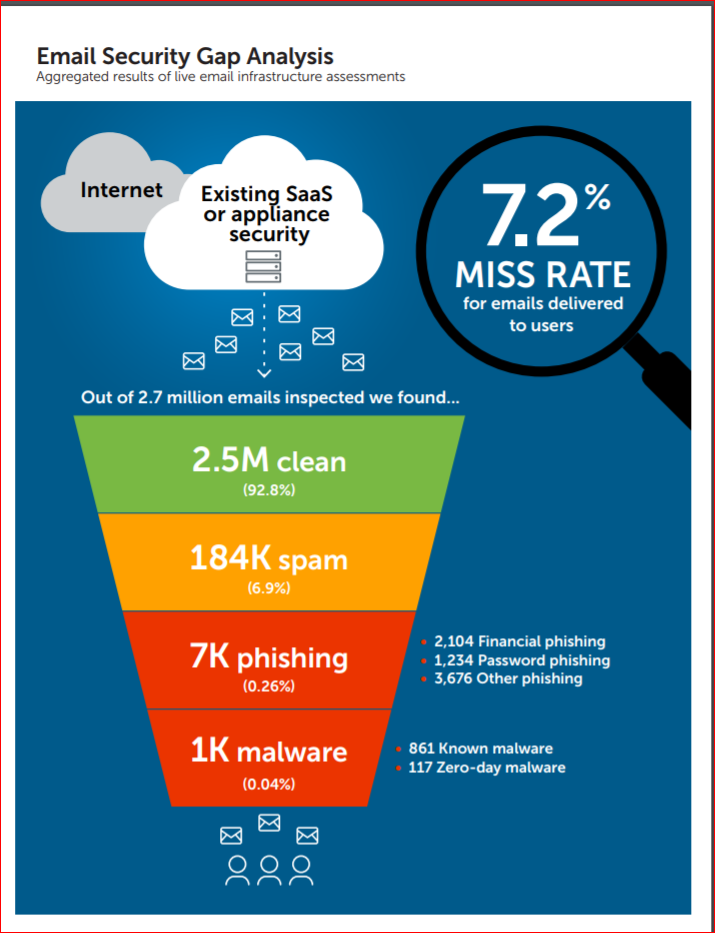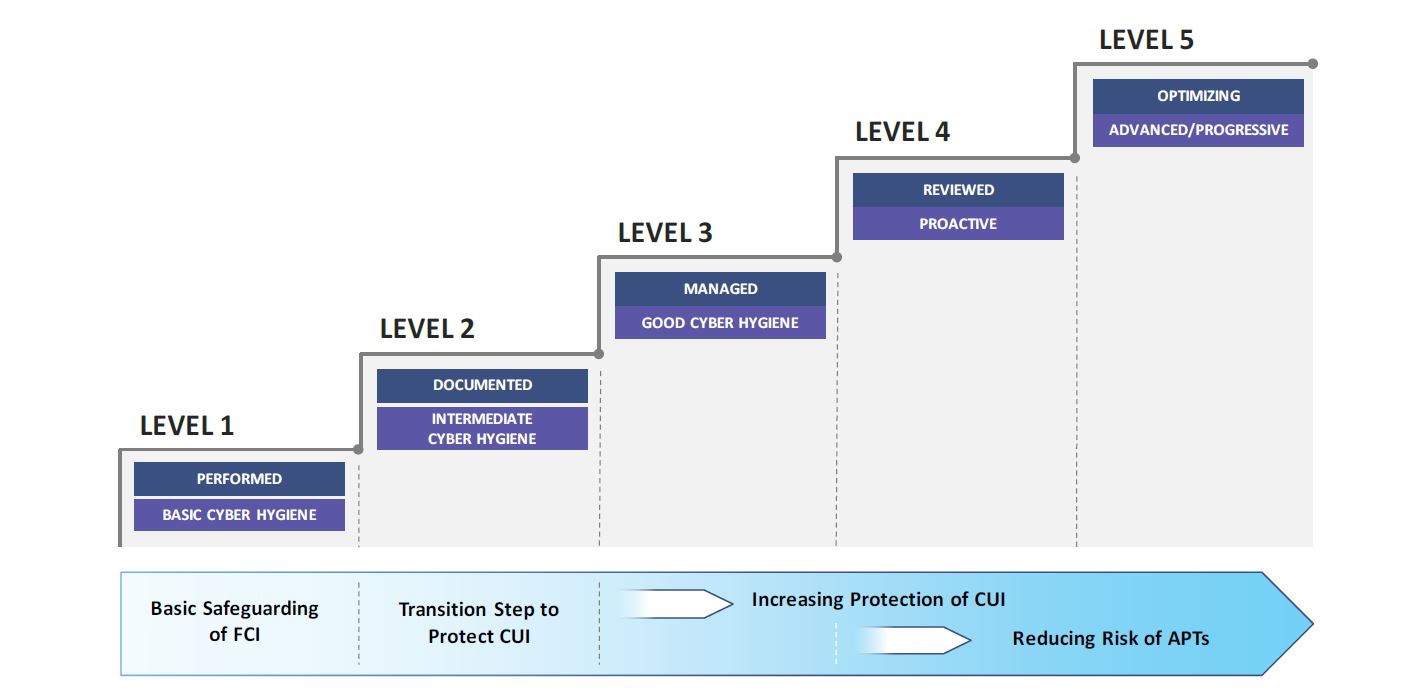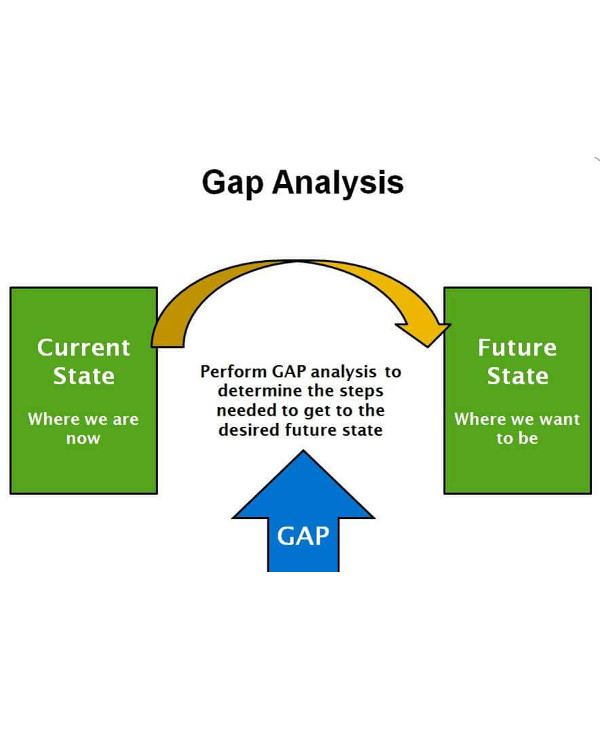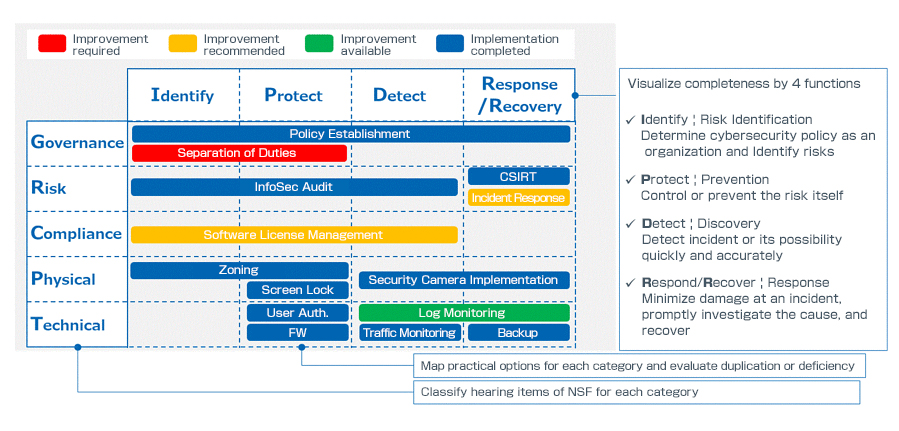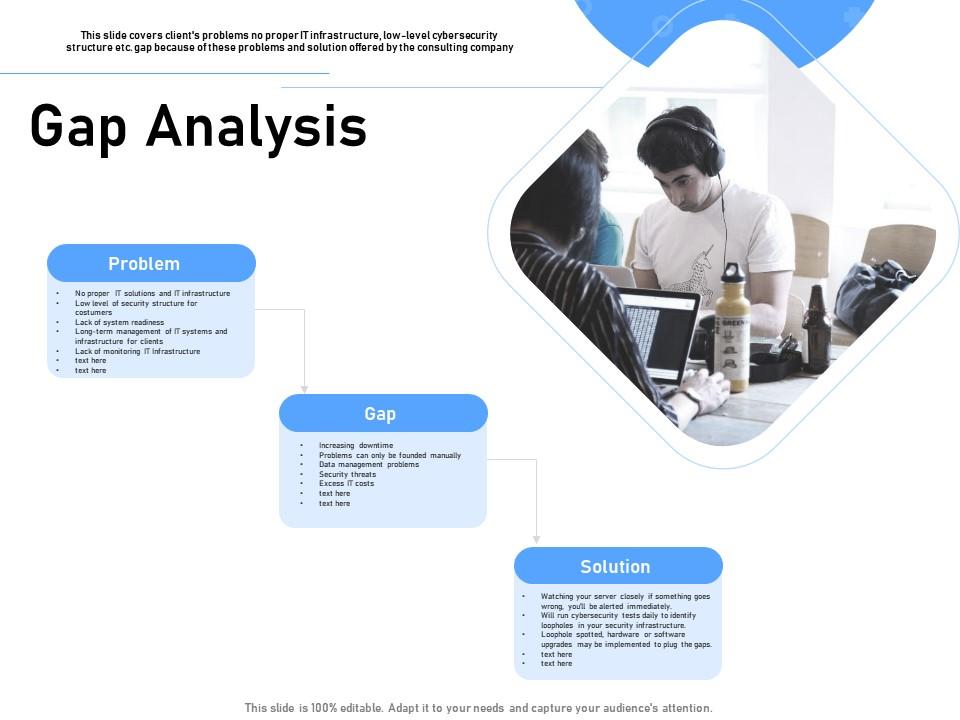
Gap Analysis Security Threats Ppt Powerpoint Presentation Background Images | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
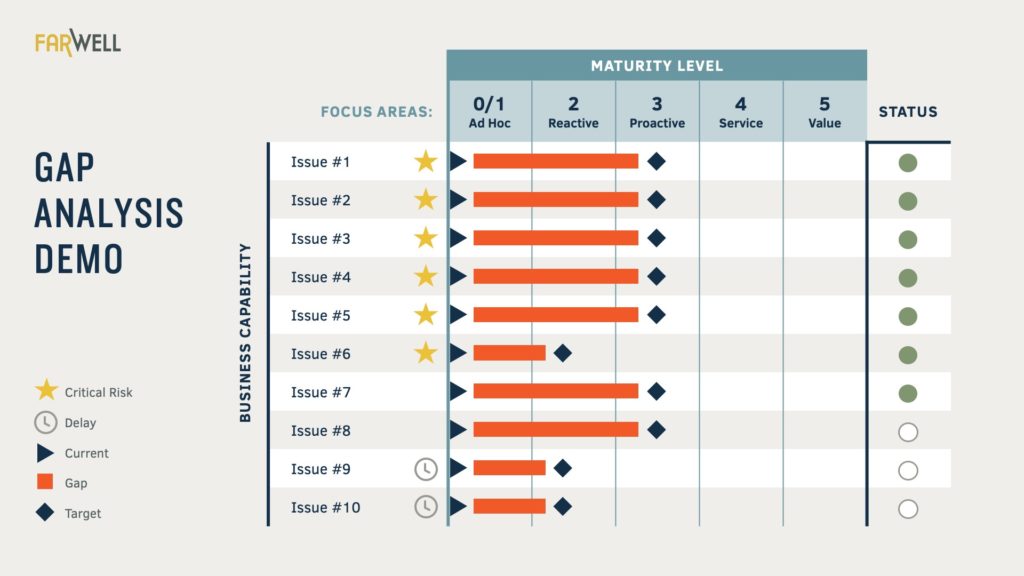
Health Care Management Organization Performs Gap Analysis to Modernize and Mitigate Data Security Risks - FarWell